Kubernetes Multi-cluster Service Mesh using Istio – which implementation fits your case?
KubeCon 2023 is an excellent opportunity for learning and exploring new ideas in Kubernetes and cloud-native technologies. One area of particular interest is service mesh, a transformative technology that enhances scalability, security, and observability in modern applications. Through dedicated sessions and workshops, KubeCon empowers attendees to delve into the intricacies of service mesh architectures and harness their potential. This article is inspired by the conversations about Service Mesh I attended.
What are Service Mesh and Istio?
A service mesh is a dedicated infrastructure layer that manages the communication between microservices in a distributed system, ideal for microservices architectures.
It helps to offload common functionality such as load balancing, service discovery, and security from the individual services, improving their performance and scalability.
Service mesh is approaching to solve several challenges that arise in microservices architectures. Here are some of the challenges that service mesh is trying to address:
- Service-to-service communication – In a microservices architecture, many different services often need to communicate with each other. Service mesh provides a solution to manage this communication by offering traffic routing, load balancing, and service discovery features.
- Security – With many services communicating with each other, it becomes challenging to ensure that all of these communications are secure. Service mesh provides features such as mTLS (mutual TLS) authentication, authorization, and encryption to help with security.
- Observability – As the number of services in a microservices architecture grows, it becomes more challenging to observe and understand how these services interact. Service mesh provides features such as distributed tracing, metrics collection, and logging to help with observability.
Ultimately, service mesh is trying to address the challenges that arise in microservices architectures by providing a way to manage service-to-service communication, observe how services interact, ensure that these communications are secure, and manage the complexity that comes with microservices architectures.
However, the implementation of Service Mesh does bring an additional layer of complexity to the system. Obviously, there will likely be a knowledge gap to close.
There are a few known options for service mesh implementations, such as Istio, Linkerd, Consul, AWS App Mesh, and more. However, in this article, we’ll focus on Istio.
So, Istio is an open-source service mesh solution that provides a platform-independent and extensible way to manage service-to-service communication within a cloud-native environment. Istio supports multiple languages, runtimes, and platforms, making it a popular choice for many organizations.
Let’s talk about multi-cluster architecture
In a multi-cluster environment, multiple Kubernetes clusters are deployed in different locations, each with its own set of microservices deployed. These clusters can be located in different regions or even in different cloud providers, making it challenging to manage communication between them.
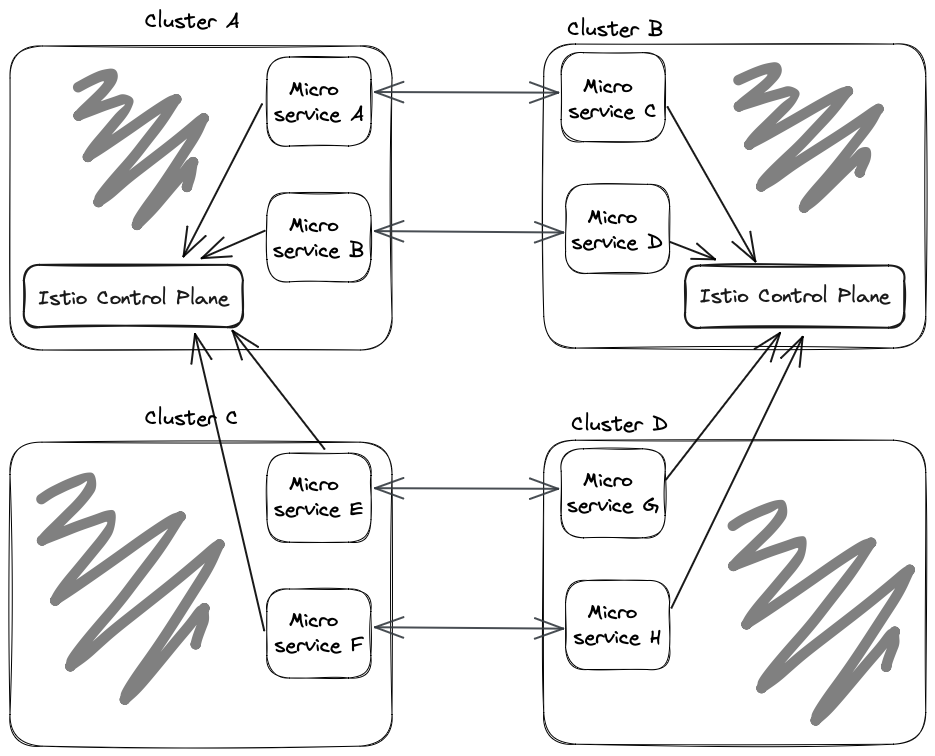
This very simplified drawing below is an example of the situation when possibly Microservices A & B will try to communicate with Microservices C & D.
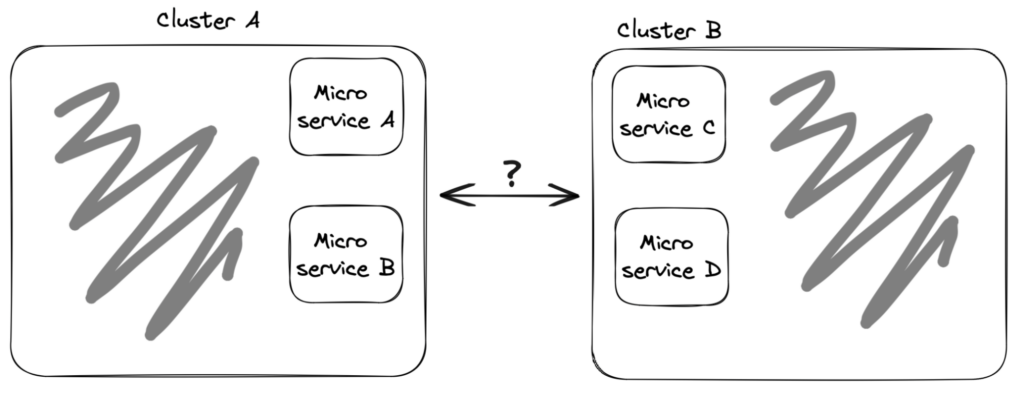
* The illustrations in this article are super simplified for understanding the high-level methodology. There are many details missed, such as Kubernetes networking basics (such as Services), Istio components (such as sidecars), and more.
A service mesh like Istio can help to manage communication between services in different clusters.
By using Istio, you can establish a unified service mesh across all clusters, allowing you to manage communication between services in different clusters using the same set of tools and policies.
Istio components for multi-cluster communication
To enable communication between services in different clusters, Istio provides several components:
- Istio Gateway – This component provides an entry point for traffic into the mesh. It is responsible for routing external traffic to the appropriate services in the mesh.
- VirtualService – This component defines the rules for traffic routing within the mesh. It can route traffic based on URL, HTTP headers, or other criteria. Each routing rule defines matching criteria for the traffic of a specific protocol. If the traffic is matched, it is sent to a named destination service (or subset/version of it) defined in the registry.
- DestinationRule – This component defines the policies that govern how traffic is routed to a specific destination. It defines policies that apply to traffic intended for service after routing has occurred. It can be used to specify load-balancing algorithms, connection timeouts, and other settings.
These Istio components are the base for routing traffic between services in different clusters based on a set of rules and policies.
Benefits of Istio for multi-cluster communication
Using Istio for multi-cluster communication can provide several benefits, including:
- Improved reliability – Istio provides advanced traffic management features such as load balancing and circuit breaking, which can help to ensure that services in different clusters can communicate reliably
- Increased security – Istio provides features such as mutual TLS that can help to secure communication between services in different clusters
- Better scalability – By offloading common functionality such as load balancing and service discovery to Istio, individual services can be scaled more easily
- Data locality – By using multi-cluster architecture and service mesh implementation, you can separate the data from the application level for data locality reasons. Sometimes there is a need to separate geographically the data from the application level, i.e. when data must be saved in Europe, but we want to run an application in US for lower server costs
Real-world use cases for Istio in multi-cluster environments include managing communication between on-premises and cloud-based services, managing communication between services in different regions, and managing communication between services in different cloud providers.
Istio multi-cluster implementation types
There are several types of multi-cluster implementation using Istio, each with its benefits and trade-offs. Here are the most common types:
Multi-Primary
In a Multi-Primary Cluster deployment, each cluster has its own Istio control plane, which operates independently of the others. This type of deployment is ideal for scenarios where clusters have different security requirements or operate in different regions.
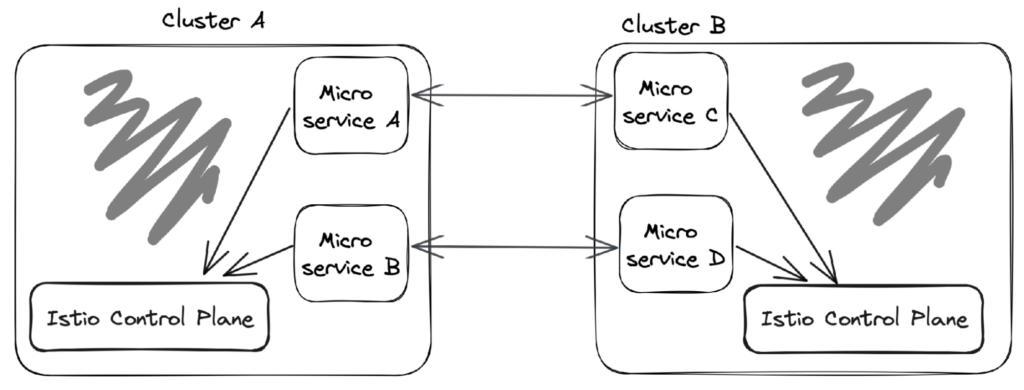
Benefits
- Each cluster is independent and can be managed separately
- Provides fault isolation between clusters
- Can be deployed across regions or cloud providers for better resilience and availability
Trade-offs
- Requires more resources to operate multiple control planes
- More complex to set up and manage
- Difficult to maintain consistent configurations across all clusters
Primary-Remote (Shared Control Plane)
In a Primary-Remote (Shared Control Plane) deployment, multiple clusters share a single Istio control plane, allowing them to operate as a single service mesh. This type of deployment is ideal for scenarios where clusters need to operate as a unified system and share the same configuration.
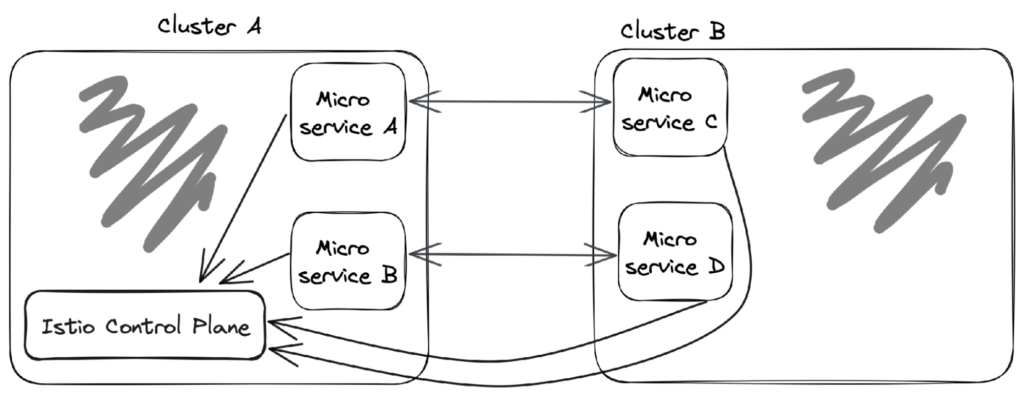
Benefits
- Simplifies configuration management and policy enforcement
- Reduces resource requirements compared to a multi-primary cluster deployment
- Allows for better visibility across all clusters.
Trade-offs
- Increases the risk of a single point of failure
- Clusters must operate within the same security requirements
- Scaling can be challenging as all clusters are managed by a single control plane
Hybrid
In a Hybrid deployment, multiple clusters are deployed in different modes, with some clusters using a multi-primary cluster model and others using a shared control plane model. This deployment type is ideal for scenarios where clusters have different security, governance, or data locality requirements.
Benefits
- Provides flexibility to manage clusters with different requirements
- Reduces resource requirements compared to a fully shared control plane deployment
- Enables better resilience and availability by distributing clusters across regions or cloud providers.
Trade-offs
- More complex to set up and manage
- Requires careful planning to ensure consistent configurations across all clusters
- It can be more challenging to monitor and troubleshoot
Each of these multi-cluster deployment models can be implemented using Istio, and the choice of which model to use depends on the specific requirements of the system being deployed. Ultimately, the key is choosing a model that balances flexibility, manageability, and reliability for the specific use case.
To get started with Istio for multi-cluster communication, you have to deploy Istio in each cluster and configure it to use the desired control plane mode you chose. You also have to configure Istio Gateway, VirtualService, and DestinationRule components to route traffic between services in different clusters.
The Istio documentation provides detailed instructions on deploying Istio in a multi-cluster environment and best practices for configuring Istio for optimal performance and reliability.
Leveraging Istio
In conclusion, Istio is a powerful service mesh solution that can help to manage communication between services in a multi-cluster environment. By providing a unified service mesh across all clusters, Istio enables you to manage communication between services using the same set of tools and policies. By offloading common functionality such as load balancing and security to Istio, individual services can be scaled more easily and communication can be made more reliable and secure.